App Passwords
App Passwords are very strong, randomly-generated passwords for use in email clients and apps, to help make your email apps more secure since they can't be protected by Two-Factor Authentication (2FA). 2FA is a secure way for a user to sign in to Webmail or MDaemon Remote Administration (MDRA), but an email app can't use it, because the app must be able to access your email in the background without you having to enter a code from your authenticator app. The App Passwords feature allows you to create strong, secure passwords for use in your apps, while still keeping your account password secured by 2FA. App Passwords can only be used in email apps, they cannot be used to sign in to Webmail or MDRA. This means that even if an App Password were somehow compromised, the unauthorized user still wouldn't be able to get into your account to change your password or other settings, but you, however, would still be able to sign in to your account with your account password and 2FA, to delete the compromised App Password and create a new one if needed.
If you do not wish to allow a user to use App Passwords, you can do so by disabling the ...edit app passwords option on the user's Web Services page. If you wish to disable support for App Passwords for all users, you can do so using the Enable app passwords option on the Passwords page.
App Password requirements and recommendations
•In order to create App Passwords, 2FA must be enabled for the account (although you can turn off this requirement if you choose).
•App Passwords can only be used in email apps—they cannot be used to sign in to Webmail or MDRA.
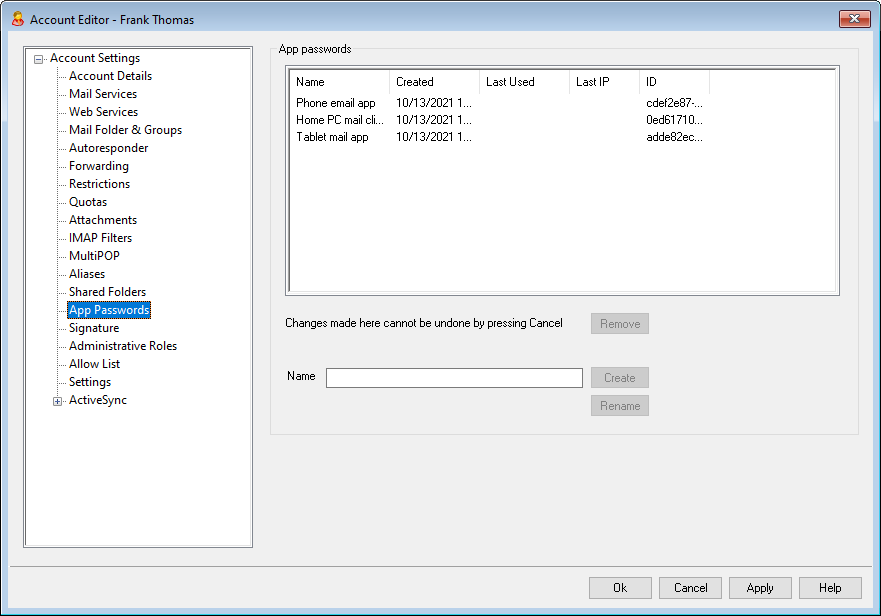
•Each App Password is displayed only once, when it is created. There is no way to retrieve it later, so users should be ready to enter it into their app when it is created.
•Users should use a different App Password for each email app, and they should revoke (delete) its password whenever they stop using an app or when a device is lost or stolen.
•Each App Password lists when it was created, when it was last used, and the IP address from which it last accessed the account's email. If a user finds something suspicious about the Last Used or Last IP data, the user should revoke that App Password and create a new one for his or her app.
•When an account password is changed, all App Passwords are automatically deleted—a user cannot continue using old App Passwords.
Creating and using App Passwords
User's will typically create and manage their own App Passwords from within Webmail following the steps outlined below (this information is included in the Webmail help file). Before the user begins, he should have his email app or client ready to enter the password, because the App Password will only be displayed once while creating it.
1.Have the app or email client ready to enter the App Password.
2.Sign in to Webmail and click Options » Security.
3.Enter the account password in Current Password.
4.Click New App Password.
5.Enter the name of the app that will use this password (e.g. "Phone email app"), and click OK.
6.Copy/paste or manually enter the displayed password into the email app, or paste it into a text file or write it down if necessary. If one copies the password to use later then he should delete the copy after entering it into his email client. When finished, click OK.
If for some reason you need to create or delete an App Password for one of your users, you can do so using the options on this page. Just as in Webmail, the App Password will only be displayed once when it is created, so it should immediately be entered into the app or copied somewhere to give to the user later.
|
There is an account option on the Account Editor's Settings page that you can use to "Require app password to log in to SMTP, IMAP, ActiveSync, etc." Requiring App Passwords can help protect an account's password from dictionary and brute force attacks via SMTP, IMAP, etc. This is more secure because even if an attack of this sort were to guess an account's actual password, it wouldn't work and the attacker wouldn't know, because MDaemon would only accept a correct App Password. Additionally, if your accounts in MDaemon are using Active Directory authentication and Active Directory locks an account after a number of failed attempts, this option can help prevent accounts from being locked out, because MDaemon will only check the App Passwords, not try to authenticate to Active Directory. |
See:
