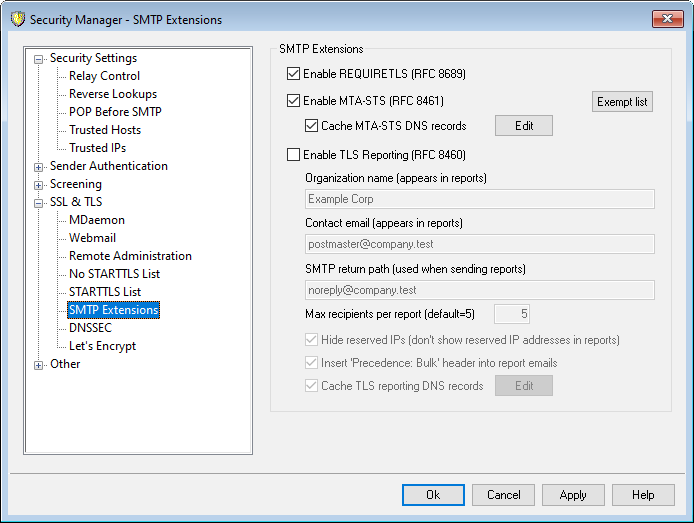
SMTP Extensions
Enable REQUIRETLS (RFC 8689)
RequireTLS allows you to flag messages that must be sent using TLS. If TLS is not possible (or if the parameters of the TLS certificate exchange are unacceptable) messages will be bounced rather than delivered insecurely. For a complete description of RequireTLS, see: RFC 8689: SMTP Require TLS Option.
RequireTLS is enabled by default, but the only messages that will be subject to the RequireTLS process are messages specifically flagged by a Content Filter rule using the new Content Filter action, "Flag message for REQUIRETLS...", or messages sent to <local-part>+requiretls@domain.tld (for example, arvel+requiretls@mdaemon.com). All other messages are treated as if the service is disabled. Several requirements must be met in order for a message to be sent using RequireTLS. If any of them fail, the message will bounce back rather than be sent in the clear. The requirements are:
•RequireTLS must be enabled.
•The message must be flagged as needing the RequireTLS treatment, via the Content Filter action or the "<localpart>+requiretls@..." address.
•DNS lookups for recipient MX hosts must use DNSSEC (see below), or the MX must be validated by MTA-STS.
•The connection to the receiving host must use SSL (STARTTLS).
•The SSL certificate of the receiving host must match the MX host name and chain to a trusted CA.
•The receiving mail server must support REQUIRETLS and say so in the EHLO response.
RequireTLS requires DNSSEC lookups of MX record hosts, or the MX must be validated by MTA-STS. You can configure DNSSEC by specifying criteria whereby lookups will request DNSSEC service. MDaemon's IP Cache has an option for accepting DNSSEC assertions, and there are DNSSEC related instructions at the top of the MX Hosts file. Finally, DNSSEC requires appropriately configured DNS servers, which is beyond the scope of this help file.
MTA-STS support is enabled by default and is described in RFC 8461: SMTP MTA Strict Transport Security (MTA-STS).
SMTP MTA Strict Transport Security (MTA-STS) is a mechanism enabling mail service providers (SPs) to declare their ability to receive Transport Layer Security (TLS) secure SMTP connections and to specify whether sending SMTP servers should refuse to deliver to MX hosts that do not offer TLS with a trusted server certificate. To set up MTA-STS for your own domain, you will need an MTA-STS policy file that can be downloaded via HTTPS from the URL https://mta-sts.domain.tld/.well-known/mta-sts.txt, where "domain.tld" is your domain name. The policy text file should contain lines in the following format:
version: STSv1
mode: testing
mx: mail.domain.tld
max_age: 86400
Mode can be "none", "testing", or "enforce". There should be an "mx" line for each of your MX hostnames. A wildcard can be used for subdomains, such as "*.domain.tld". Max age is in seconds. Common values are 86400 (1 day) and 604800 (1 week).
Also needed is a DNS TXT record at _mta-sts.domain.tld, where "domain.tld" is your domain name. It must have a value in the format:
v=STSv1; id=20200206T010101;
The value for "id" must be changed every time the policy file is changed. It is common to use a timestamp for the id.
Exempt List
Use this list to make specific domains exempt from MTA-STS.
Cache MTA-STS DNS records
By default MDaemon caches MTA-STS DNS records. Click Edit to view or edit the current cache file.
Enable TLS Reporting (RFC 8460)
TLS Reporting is disabled by default and discussed in RFC 8460: SMTP TLS Reporting.
TLS Reporting allows domains using MTA-STS to be notified about any failures to retrieve the MTA-STS policy or negotiate a secure channel using STARTTLS. When enabled, MDaemon will send a report daily to each STS-enabled domain that it has sent (or attempted to send) mail to that day. There are several options provided for configuring the information that your reports will contain.
To set up TLS Reporting for your domain, enable DKIM signing, and create a DNS TXT record at _smtp._tls.domain.tld, where "domain.tld" is your domain name, with a value in the format:
v=TLSRPTv1; rua=mailto:mailbox@domain.tld
Where mailbox@domain.tld is the email address where you want reports for your domain to be sent.