
MDaemon's built-in web server supports the Secure Sockets Layer (SSL) protocol. SSL is the standard method for securing server/client web communications. It provides server authentication, data encryption, and optional client authentication for TCP/IP connections. Further, because HTTPS support (i.e. HTTP over SSL) is built into all major browsers, simply installing a valid digital certificate on your server will activate the connecting client's SSL capabilities.
The options for enabling and configuring Webmail to use HTTPS are located on the SSL & HTTPS screen under Setup » Web & IM Services » Webmail". For your convenience, however, these options are also mirrored under "Security » Security Manager » SSL & TLS » Webmail".
For more information on the SSL protocol and Certificates, see: SSL & Certificates
|
This screen only applies to Webmail when using MDaemon's built-in web server. If you configure Webmail to use some other web server such as IIS, these options will not be used — SSL/HTTPS support will have to be configured using your the other web server's tools. |
Accept the Following Connection Types
HTTP only
Choose this option if you do not wish to allow any HTTPS connections to Webmail. Only HTTP connections will be accepted.
HTTP and HTTPS
Choose this option if you want to enable SSL support within Webmail, but do not wish to force your Webmail users to use HTTPS. Webmail will listen for connections on the HTTPS port designated below, but it will still respond to normal http connections on the Webmail TCP port designated on the Web Server screen of Webmail.
HTTPS only
Choose this option if you wish to require HTTPS when connecting to Webmail. Webmail will respond only to HTTPS connections when this option is enabled — it will not respond to HTTP requests.
HTTP redirected to HTTPS
Choose this option if you wish to redirect all HTTP connections to HTTPS on the HTTPS port.
HTTPS port
This is the TCP port that Webmail will listen to for SSL connections. The default SSL port is 443. If the default SSL port is used, you will not have to include the port number in Webmail's URL when connecting via HTTPS (i.e. "https://example.com" is equivalent to "https://example.com:443").
|
This is not the same as the Webmail port that is designated on the Web Server screen of Webmail. If you are still allowing HTTP connections to Webmail then those connections must use that other port to connect successfully. HTTPS connections must use the HTTPS port. |
Select certificate to use for HTTPS/SSL
This box displays your SSL certificates. Check the box next to any certificates you wish to be active. Click the star next to the one that you wish to set as the default certificate. MDaemon supports the Server Name Indication (SNI) extension to the TLS protocol, which allows a different certificate to be used for each of your server's host names. MDaemon will look at the active certificates and choose the one that has the requested host name in its Subject Alternative Names field (you can specify the alternate names when creating the certificate). If the client does not request a host name, or if no matching certificate is found, then the default certificate is used. Double-click a certificate to open it in Windows' Certificate dialog for review (only available in the application interface, not in the browser-based remote administration).
Delete
Select a certificate in the list and then click this button to delete it. A confirmation box will open and ask you if you are sure that you want to delete the certificate.
Create Certificate
Click this button to open the Create SSL Certificate dialog.
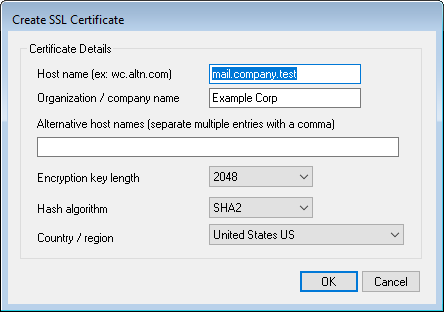
Certificate Details
Host name
When creating a certificate, enter the host name to which your users will connect (for example, "wc.example.com").
Organization/company name
Enter the organization or company that "owns" the certificate here.
Alternative host names (separate multiple entries with a comma)
If there are alternative host names to which users may be connecting and you want this certificate to apply to those names as well, then enter those domain names here separated by commas. Wildcards are permitted, so "*.example.com" would apply to all sub domains of example.com (for example, "wc.example.com", " mail.example.com", and so on).
|
MDaemon supports the Server Name Indication (SNI) extension to the TLS protocol, which allows a different certificate to be used for each of your server's host names. MDaemon will look at the active certificates and choose the one that has the requested host name in its Subject Alternative Names field. If the client does not request a host name, or if no matching certificate is found, then the default certificate is used. |
Encryption key length
Choose the desired bit-length of the encryption key for this certificate. The longer the encryption key the more secure the transferred data will be. Note, however, that not all applications support key lengths longer than 512.
Country/region
Choose the country or region in which your server resides.
Hash algorithm
Choose the hash algorithm that you wish to use: SHA1 or SHA2. The default setting is SHA2.
Restart web server
Click this button to restart the web server. The web server must be restarted before a new certificate will be used.
Using Let's Encrypt to Manage Your Certificate
Let's Encrypt is a Certificate Authority (CA) that provides free certificates via an automated process designed to eliminate the currently complex process of manual creation, validation, signing, installation, and renewal of certificates for secure websites.
To support using Let's Encrypt's automated process to manage a certificate, the Let's Encrypt screen is provided to help you easily configure and run the PowerShell script included in the "MDaemon\LetsEncrypt" folder. Running the script will set up everything for Let's Encrypt, including putting the necessary files in the Webmail HTTP folder to complete the http-01 challenge. It uses the SMTP host name of the default domain as the domain for the certificate, includes any Alternate host names you have specified, retrieves the certificate, imports it into Windows, and configures MDaemon to use the certificate for MDaemon, Webmail, and Remote Administration. Further, the script creates a log file in the "MDaemon\Logs\" folder, called LetsEncrypt.log. This log file is removed and recreated each time the script runs, and it includes the starting date and time of the script. Also, notification emails will be sent when errors occur if you specify an Admin email for notifications. See the Let's Encrypt topic for more information.
See:
Creating and Using SSL Certificates
